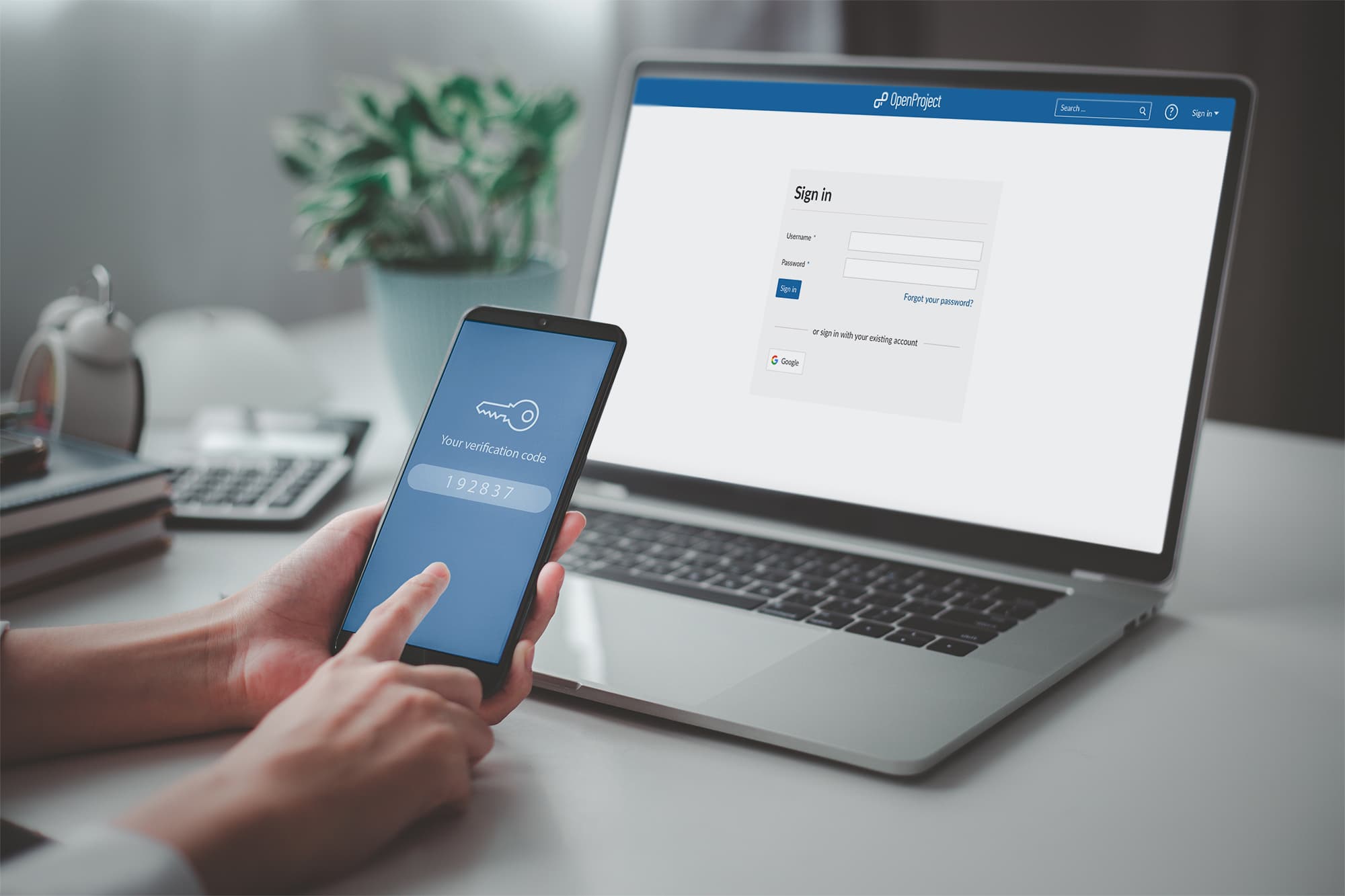
Multi-factor authentication to improve data security
Working with a project management software has probably made you very aware of data security and privacy because project management includes dealing with a lot of sensitive information - from business processes, to customers, staff etc. Whether you are using the software in the cloud or on-premises, you want your confidential data to be protected.
Cyber criminals are trying to steal data on a daily basis. It is their job and through AI and machine learning cyberattacks have become very professional and efficient and security threats are bigger than ever before.
Hence, an effective data security strategy is imperative to not become a victim of data theft. Thereby, multi-factor authentication needs to be part of your strategy and part of your catalogue of requirements when selecting a software.
Multi-factor authentication has always been part of OpenProject’s Enterprise security feature set and will now be extended to our free Community edition. It will be released with OpenProject 12.4. Before going into detail, let’s have a look at multi-factor authentication overall, its importance and different types.
What is multi-factor authentication?
Single-factor authentication asks users only for one verification factor, e.g. a password, to gain access to a system. Cyber criminals can hack this information more easily and then get access to confidential data.
Multi-factor authentication is part of an organization’s identity and access management. It proves that the user’s identity is legitimate by using two or more factors. When logging in to an application, online account, VPN or the likes, the user needs to not only provide username and password, but minimum one additional verification factor.
Multi-factor and 2-factor authentication
Two-factor is a multi-factor authentication where only two factors are required to prove your identity. Multi-factor authentication can use two factors or more.
Why do you need multi-factor authentication?
The ever-increasing use of web-based cloud services as well as remote work with users logging in remotely from anywhere at anytime, calls for increased data security. That is because critical data could become vulnerable to unauthorized persons gaining access from anywhere at anytime. Before, an additional security factor was limiting access to users being physically on the same network as the system.
Multi-factor authentication makes user accounts more secure. It prevents unauthorized persons to gain access to user accounts and consequently reduces the risk of fraud and cyberattacks.
What does multi-factor authentication do?
Multi-factor authentication drastically decreases the risk of cyberattacks that involve obtaining account credentials. This includes phishing, spear phishing, keyloggers, credential stuffing, brute force and reverse brute force attacks, man-in-the-middle (MITM) attack.
Benefits of multi-factor authentication
Overall, multi-factor authentication adds an additional verification layer to protect access to the system and hence adds to fighting cyberattacks.
Thereby, it offers the following advantages:
- Reduces risk from compromised passwords
Passwords are the least secure option to manage access to a system because people use simple passwords, use the same passwords over and over again, share passwords and so much more.
- Provides a unique security solution
Depending on each use case, the organization can choose to have two or more authentication factors. Thereby, also the type of authentication (fingerprint, code etc.) can be selected according to the organization’s needs.
- Can be used with single sign-on
When using multi-factor authentication with single sign on, it improves the security and is convenient for the user because they only need to sign in once.
- Helps to achieve regulatory compliance
Many regulations require multi-factor authentication. By implementing this security protocol allows an organization to meet these requirements.
- Enables remote work
With teams working remotely and logging in from anywhere at anytime, multi-factor authentication increases data security and allows this (new) way of working.
What different ways of multi-factor authentication are there?
There are three principal ways how users are authenticated.
-
Knowledge: Things you know, e.g. username and password.
-
Possession: Things you have, e.g. a mobile phone or a card.
-
Inherence: Things you are, e.g. fingerprint, voice or retina.
Thereby, a combination of these factors can be used to authenticate a user.
Newer ways of multi-factor authentication furthermore include:
-
Location: the location of the user is checked before giving access, this could be e.g. the IP address or geo location. If the user is e.g. in an unusual location the system could ask for an additional form of authentication to verify the user’s identity.
-
Adaptive authentication or risk-based authentication: Context and behavior of the user are analyzed when authenticating, e.g. is the user using the same log in device as the day before or is the user trying to gain access during their normal work hours. Depending on the information, a risk level is assigned to the login attempt and the user is either asked for an additional authentication factor or not.
OpenProject two-factor authentication
Using a project management software like OpenProject means a lot of confidential information is getting processed. This data needs to be protected under all circumstances. OpenProject’s mission is to ensure the utmost security and protection of your personal data.
That is why we offer two-factor authentication that will prevent anyone from accessing or using your account and adds an additional level of security to your project organization.
Two-factor authentication has always been available for OpenProject Enterprise cloud and on-premises. And because OpenProject stands for data security and privacy, we now make this security feature also available for our free Community edition. This will happen with the release of OpenProject 12.4.
Rest assured that OpenProject does everything to protect your data and strives to provide you with data sovereignty.


